Workshop Objective: The most accessible segment of a mobile network is Radio Access Network or RAN, which handle the subscriber signals. In this talk, we will demonstrate mobile Radio Access Network concepts and talk about weaknesses, vulnerabilities, risks and practical hacking scenarios.
Read MoreWorkshop Objective: Today all vehicles are connected through V2X technologies. All manufacturers are coming with new technologies which can be added technologies for Vehicle industries like Fleet management systems, diagnosis toolset etc.
Read MoreWorkshop Objective: This course is ideal for those intending to expand their knowledge about mobile app security as it covers a large number of topics: People relatively new to mobile security will benefit from the practical deep dive while more advanced students can polish their skills in specific areas and perhaps complete....
Read MoreWorkshop Objective: An organization using micro services, or any other distributed architecture rely heavily on containers and orchestration engines like Kubernetes and as such its infrastructure security is paramount to its business operations. This workshop will focus on how attackers can break into docker.....
Read MoreWorkshop Objective: Amazon Web Services (AWS) one of the most popular cloud service. There is a need for security testers, Cloud/IT admins and people tasked with the role of DevSecOps to learn on how to effectively attack and test their cloud infrastructure. In this training we will cover attack approaches........
Read MoreWorkshop Objective: Secure code audit is a highly effective process of identifying vulnerabilities in software. This process requires a more in-depth analysis of an application in order to find the security flaws. This training will be hands on on how to do secure code analysis & review.....
Read MoreWorkshop Objective: It is important to keep pace with the attack vectors of today and tomorrow. So, we need a solution which helps us to hunt for a needle in a haystack. Building a solution which collates, sanitizes and stores security event information, will enable further analysis by a SOC Analyst – using a single pane of glass........
Read MoreWorkshop Objective: Nowadays, hardware and operating system (OS) securities have become more robust, so hackers and researchers look for exploits in other areas such as firmware. Many IoT devices become vulnerable to cyber attacks because their firmware isn’t updated. One of the instances where we might have heard of ........
Read MoreWorkshop Objective: Dissecting and exploiting BLE device 101 is built for anyone who wants to get started with BLE security testing, understating the BLE internals, and the packet format of Bluetooth Low Energy devices which helps the attendees to understand, enumerate and exploit the BLE smart devices.
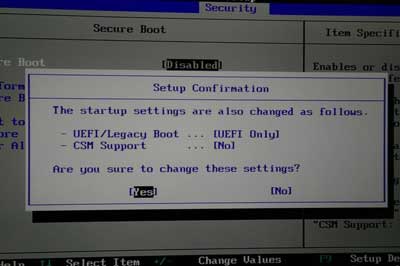
Read MoreWorkshop Objective: The operating system is the main working space of a computer. But it is not the first system which is launched your computer. Previously, an UEFI (descendant of the BIOS) permits to set up the system and its main configuration. This system is not just a short state but a .......
Read MoreWorkshop Objective: Reverse engineering is a quite important business since it allows users to understand how systems work. It matters is the case of malware analysis, vulnerabilities exploitation and how to break cipher systems. Following the workshop proposed in the .......
Read More